New Relic has launched enhanced options to its Interactive Utility Safety Testing (IAST) device, together with a novel proof-of-exploit reporting perform for simpler utility safety testing.
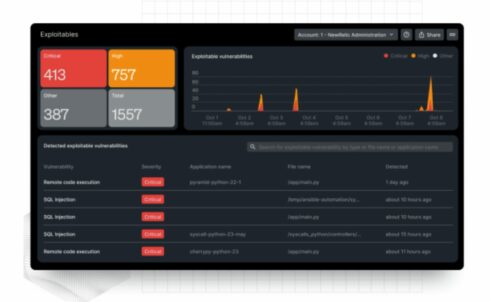
This replace permits New Relic’s customers to pinpoint exploitable vulnerabilities inside their purposes, permitting them to copy points for simpler remediation earlier than they launch new software program variations. This development aids each safety and engineering groups in concentrating their efforts on real utility safety points, making certain no false positives, in accordance with New Relic.
The introduction of proof-of-exploit reporting considerably enhances the appliance safety testing course of, enabling New Relic prospects to establish, confirm, and repair exploitable vulnerabilities extra effectively.
This strategy ensures that groups can confidently deploy new code, backed by the reassurance of a 100% accuracy price in detecting actual safety issues, as validated by the industry-recognized OWASP benchmark.
“Safety have to be ingrained within the improvement tradition, not simply added on. New Relic IAST gives engineering and IT groups the flexibility to establish actual utility safety dangers with the identical platform they use to watch utility efficiency,” stated Manav Khurana, chief product officer at New Relic. “It strengthens DevSecOps by bringing builders and safety groups collectively to write down safe code that defends towards the threats of tomorrow and promotes a proactive stance on safety. For effectively over a decade, the New Relic full-stack observability platform has bridged organizational silos by offering a single, trusted supply of fact and unified consumer workflows – and now New Relic IAST furthers this mission.”
Different new updates embody a brand new threat publicity and evaluation function that gives visibility into each code change and immediate impression evaluation, which particulars the variety of purposes that might be impacted by a vulnerability.